How to implement Aadhaar Data Vault (ADV) ?
Securing Aadhaar Numbers using Aadhaar Data Vault- what it takes to build it yourself & the compliance aspect
Update - 15/07/2025: Check out an open-source implementation here.
As per the Aadhaar Act, all organizations that plan to store customer / employee Aadhaar numbers should use a secure storage mechanism to avoid misuse. Aadhaar number, in particular, is vulnerable as it uniquely identifies the residents of India. The majority of the Aadhaar leak incidents we witnessed in the last decade resulted from poor management of Aadhaar numbers in systems of various government & private agencies. UIDAI has come up with the following guidelines
Aadhaar numbers should be stored in a separate database (a vault) encrypted using algorithms such as RSA 2048, AES 256, etc.
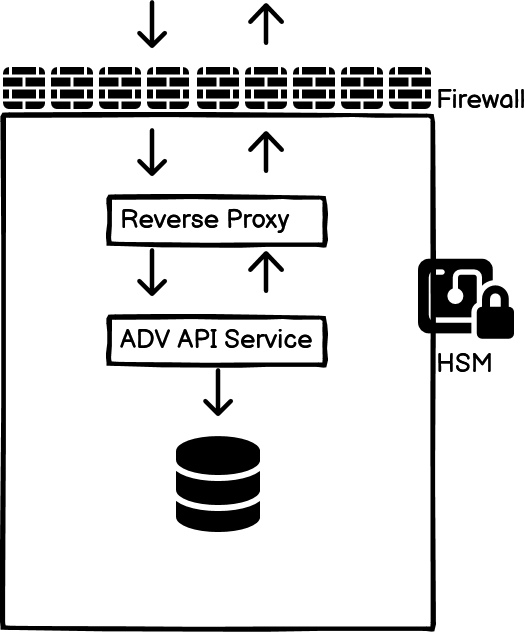
The vault system should be hosted on an isolated VLAN from your other systems.
The vault should maintain a unique reference key against each Aadhaar number stored. This reference key should be stored in all other databases instead of the Aadhaar Number.
The encryption keys for the ADV should be maintained in the Hardware Security Module (HSM)
There are several vendor solutions available in the market. However, if you have an engineer with a few days of spare time, you can build one yourself using the steps below.
Use your favourite open-source database, such as MySQL / PostgreSQL, and create the following tables
API_USER for authenticating Aadhaar Data Vault (ADV) API Clients. It can have api_key, api_secret, client_name, active & created datetime fields
A_VAULT for storing encrypted aadhaar number against the reference key
EVENT_LOG for maintaining access logs. It can have api_key, operation_type (fetch/insert), reference key and datetime fields.
Use your favorite server side programming language to expose the REST APIs
registration service for registering ADV client and generating the access key and token
store service for storing the Aadhaar number. The store service should use a UUID generator for the reference key and RSA 2048 (asymmetric) / AES 256 (symmetric) algorithm for encrypting the Aadhaar number. The store service should also log an entry in the EVENT_LOG table. The store service should return the reference key to the API client.
fetch service for retrieving the Aadhaar number based on the reference key. This service should decrypt the stored Aadhaar number and log the fetch action in the EVENT_LOG table before sending the Aadhaar number to the client. Vice versa, the fetch service should also retrieve the reference key for a given Aadhaar number.
Make sure you maintain the encryption keys in a Hardware Security Module (HSM). If you are deploying your ADV solution on-cloud such as AWS / Google Cloud, you can make use of their Cloud HSM service for storing the encryption keys. Alternately, if you are deploying the ADV solution on your datacenter server, make sure you purchase an HSM module and attach it to your server. Use PKCS11 library to access the encryption keys from the HSM module.
Last, but not the least, do not directly expose your ADV service to the client. Instead deploy it behind a reverse proxy such as nginx / apache server.